Information Security
The IPv6 protocol creates new information security challenges, from architectural, product, implementation, and operational exposures. While the IPv6 network protocol includes many security improvements over IPv4, it also presents significant new unsolved problems for information system security. Problems include defining and controlling enclaves, designing boundary security systems, mapping network topology, conducting intrusion detection, and assessing vulnerabilities. Other issues include certification and accreditation, and security testing.
Architecture
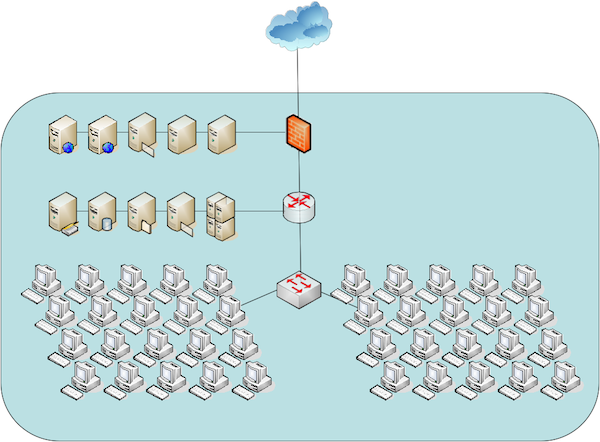
The current standard in network security is the enclave architecture. Within this architecture there is a trusted internal network (or intranet), an untrusted external network (or extranet) and a firewall to separate these. If there are public servers, they are hosted on a separate service network, also separated by the firewall. The firewall manages all the traffic that crosses between any of these networks and enforces defined security policies that specify the allowed services. IPv6 provides new security features for each host including authentication and encryption. It also provides capabilities for auto-configuration. However, these are based on individual hosts rather than enclaves. Since individual hosts can mutually authenticate each other and communicate through IPsec Virtual Private Networks (VPNs), this complicate traditional information assurance operations including controlling information flow into or out of the enclave, management of the network topology in the presence of IP mobility and dynamic routing, security monitoring of network activity, managing host vulnerability, security testing, and certification and accreditation.