Information Security
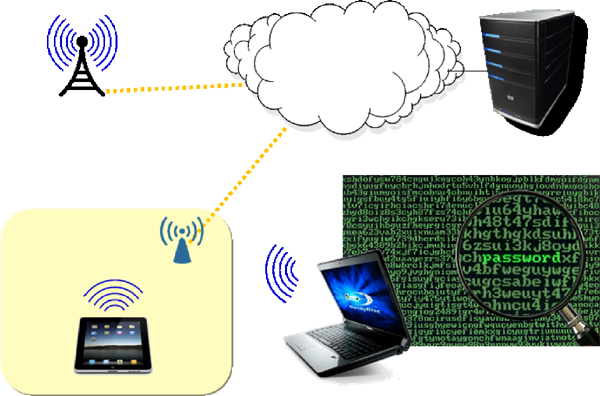
Mobile computing has specific Information security issues to be addressed in addition to the normal security requirements of desktop computing.
Device Authentication. Authentication of the mobile device needs to be reestablished whenever it reconnects to the network, since it is not physically attached to a static location on the network topology. Device certificates are used to provide strong protection against impersonation.
Intrusion Detection. Recognition of wireless network intrusion attempts by unauthorized devices and the triggering of a response. Wireless intrusion detection sensors are used to detect and respond to connection attempts from foreign devices.
Secure Communication. A secure communications channel needs to be established over wireless connections. IPSec encrypted transport channels are used to ensure privacy of connections to the Campus Area Network (CAN).
Electromagnetic Isolation. Mobile devices include multiple wireless communication technologies including cellular communications, WiFi wireless ethernet, and Bluetooth. The risks associated with any use of wireless systems within secured environments need to be assessed as part of formal approval processes to prevent unintended exposure of sensitive information to adversaries.
USB. Mobile devices typically include USB interfaces that can be connected to classified desktop or other systems. Unauthorized uses can create exposures for physical or wireless exfiltration of sensitive data.
User Authentication. The user of the mobile device needs to be authenticated, and access permissions determined, as part of the establishment of a secure user session. Strong authentication is provided by the Public Key Infrastructure (PKI) and an encapsulated second IPSec Virtual Private Network (VPN) session to Data Center servers.
Malicious Software Protection. Controlling mobile applications to protect against viruses and other malware. The authenticity, integrity, and approval status of applications is verified by a signature system.
Data Spillage Protection. The operating system protects against sensitive information being shared across applications or retained unencrypted on the mobile device where it could be compromised outside of secure application channels.
Recording. Mobile devices include integrated data, voice, and video capture and storage capabilities including microphones, cameras, and clipboards.
Privacy. Popular mobile devices and applications expose user activity to unintended surveillance and exploitation. Activity includes user location, web searches, server connections, communications (voice, chat, email), contacts, calendars, notes, photos, recordings, and other information common on mobile devices.
Device Loss. Mobile devices are vulnerable to theft or other loss resulting in their removal from the secure computing environment. Protective measures include a combination of physical, operational, and technical controls to prevent the removal of mobile devices and to respond to potential losses with appropriate responses, such as remote wipe to prevent device and infrastructure exploitation.
Device Tamper Protection. Mobile devices are vulnerable to modification or insertion of implants. Protective measures include anti-tamper measures to reduce these vulnerabilities and to increase the detectability of modifications.