Taxonomy
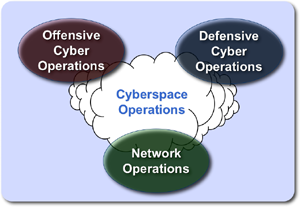
Cyberspace Operations
The cyber taxonomy provides a model to break out the primary cyberspace operations across mission areas. Today's reference model uses:Defensive Cyberspace Operations (DCO): include passive and active cyber oprations intended to defend DOD or other friendly cyberspace.
Offensive Cyberspace Operations (OCO): include cyber oeprations intended to project power by the application of force in and through cyberspace.
DoD Information Network Operations (DoDIN Ops): Includes designing, building, configuring, securing, operating, maintaining, and sustaining the operational information environment.
Net-Centric Capabilities (NCC)
Within a previous model within the defense-intelligence systems the term computer network operations (CNO) was used instead of cyber operations. CNO is organized into defend, exploit, and attack capabilities in accordance with a net-centric capabilities (NCC) model. For the purposes of this tutorial, we are covering these areas in a generic treatment, which needs to be interpreted in the context of any specific organizational mission or system capabilities.
Computer Network Defense (CND): Includes actions taken via computer networks to protect, monitor, analyze, detect and respond to network attacks, intrusions, disruptions or other unauthorized actions that would compromise or cripple defense information systems and networks. CND is conducted to some degree by every enterprise organization in both commercial and government.
Computer Network Exploitation (CNE): Includes enabling actions and intelligence collection via computer networks that exploit data gathered from target or enemy information systems or networks. CNE is conducted by authorized intelligence agencies including NSA/CSS and its partners. CNE is also conducted by adversaries of the United States.
Computer Network Attack (CNA): Includes actions taken via computer networks to disrupt, deny, degrade, or destroy the information within computers and computer networks and/or the computers/networks themselves.
Targeting Cycle
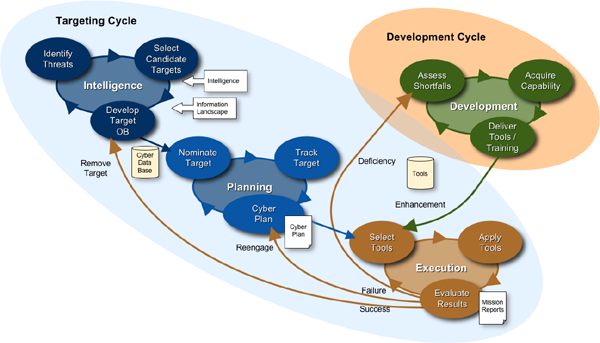
Cyber targeting operations include continuous activities covering the intelligence, planning, execution cycles and the ongoing development cycle. Each operations cycle includes concurrent processes comprising different time periods.
The long-term activities (generically referred to as Intelligence in the figure) are conducted over weeks, months, or longer durations and include analyzing intelligence and information system security information to identify and update cyber threats for engagement.
The mid-term activities (generically referred to as Planning in the figure) are conducted on a daily or longer basis and result in the cyber operations plan for the Execution.
The Development cycle is conducted in parallel to provide the business applications and tools to conduct organizational missions. Existing tools are improved and new tools are developed to address observed deficiencies.
The Execution cycle is conducted hourly during each day and includes the direct activities of the cyber operation.