Strategies
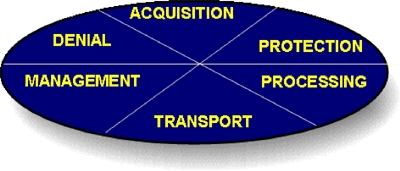
It is useful to have a context within which to evaluate strategies for cyber operations. The general information model is a simple way to do this. This model includes five elements: acquisition, protection, processing, transport, management, and denial.
Value of Information
Information is a critical factor in the success of businesses and government. It takes a wide variety of forms from mission operational data, management planning, engineering designs, manufacturing processes, financial management, personnel data bases, among other forms specific to the activity. Each type of information has a different value and different protection need.
Components of Strategy
Acquisition
An organization needs a variety of information to support is operations. These needs include planning its activities, executing its plans, monitoring its progress, and reporting its results. Information acquisition includes the entry points for information into an organization from both internal and external sources. Issues include quantity (completeness), quality (accuracy), and timeliness of this information. Business examples of acquisition systems include point-of-sale (POS) systems, market surveys, government statistics, and internal management data. Military examples of collection systems include intelligence systems, tactical radars and other sensors.
The increased reliance on information has resulted in an increasing appetite for data and new acquisition systems. By example, grocery stores introduced automated scanners to speed up the check-out process and improve its accuracy. Then they issued customers "discount and check-cashing cards" that allowed them to correlate customers with their purchasing habits.
Protection
Once information is acquired by an organization, the next logical consideration is how to protect it. The vulnerability of the "Information Infrastructure" has been widely discussed and publicized and is one important aspect of protection. Protection addresses two types of threats: information compromise and destruction. Compromise involves a competitor gaining access to an organization's proprietary data. Destruction involves the loss of this data (or loss of access to this data) as the result of a hostile attack by an adversary, or through mishandling or error.
Processing
Acquired information is processed to generate new information. Depending on the nature of the information this processing can take many forms. The quality of the algorithms and the computing power of the processing systems are significant discriminators in leveraging the available information for business objectives.
Denial
Denial includes offensive measures beyond normal protection to compromise or counter an adversary's acquisition systems. There are two types of denial: direct attacks on the adversary's information systems, and providing misinformation to his systems to induce him to take actions that are not to his advantage.
Management
An important element of the new information technologies has been the transition to new computing models: the transitions from data center mainframes to distributed computing and then to cloud computing and mobile devices. This has resulted in a decentralization of computing and data resources within organizations and the loss of central control. This creates many issues for corporate data managers, including questions of "Where is the data?", "Who has it?", and "Which version is the most current?" Other issues include deciding which data to retain (archive) for future reference, and how to store this archived data so that it will be readable by future systems. As an organization's intellectual property exists increasingly in electronic forms, it is harder to manage using traditional methods (such as conventional paper documents) and may be more easily misplaced, lost or discarded. Automated management solutions are important elements.
Transport
An essential element of cyber operations is transport. Transport involves moving data from points of acquisition to points of storage or use. The speed with which this is done affects the timeliness of the data availability and therefore the responsiveness of the organization to situations. Since this responsiveness can be a big factor in the competitive process, the speed and efficiency of an organization's transport capabilities can be an important factor in the organization's survival or failure. An example is an organization's ability to use cloud computing and e-commerce to conduct time-critical business development and customer relationship management for a competitive advantage. Competitive transport systems must be fast, reliable, and controlled. Transport considerations must be viewed within the overall cyber operations perspective, since the same efficiency that facilitates rapid message and data transportation also may be used by a competitor to download proprietary data bases in seconds or minutes.
Analysis of Strategy
An understanding of cyber operations is important to business and government organizations because it affects an organization's competitive posture. Some of the areas in which these effects are evident are capital investment, and operations.
Capital Investment
In order to be competitive in the Information age, the "smart" decisions on purchases of information systems and equipment need to include competitive considerations. Rather than simple cost-benefit analyses, an organization must consider what its competitors are doing. If they are installing electronic scanners, point-of-sale systems, then failing to do so may result in higher costs, lost revenues, or decreased market share. An organization can choose to be a leader or a follower in deploying new technologies. The worth of an investment strategy will depend heavily on factors such as capitalization or market share. It may be easier for a small company with a limited installed base and fewer sites to support to make changes to modernize its operations, whereas these same factors may complicate the fielding of any new methods or technologies.
Operations
Incorporating cyber operations into mission execution involves many choices. These choices are driven by competitiveness consideration. The aggressiveness shown by competitors in acquiring information will affect the need for processing, protection and denial. As a minimum an organization needs to incorporate a high degree of protection.